인증서 만료일자 조회
openssl s_client -connect url:port | openssl x509 -noout -dates
'IT > 기타' 카테고리의 다른 글
| [OAUTH2] 페이스북(facebook) OAuthCallbackListener 샘플 (0) | 2020.10.14 |
|---|---|
| [SAML Test] 4. Service Provider 생성 및 테스트 (0) | 2020.09.07 |
| [SAML Test] 3. Setup our Identity Provider (Docker환경에 설치) (0) | 2020.09.07 |
| [SAML Test] 1. Setup a Single Sign On SAML Test Environment with Docker and NodeJS (0) | 2020.09.07 |
| [SAML Test] 2. CentOS 8 nvm을 이용한 node.js 설치 (0) | 2020.09.07 |
[OAUTH2] 페이스북(facebook) OAuthCallbackListener 샘플
- Access Token 요청 (graph.facebook.com/oauth/access_token)
- 사용자 게시물 피드 조회 : /{user-id}/feed (graph.facebook.com/v2.5/me/feed)
'IT > 기타' 카테고리의 다른 글
| 인증서 만료일자 조회 (0) | 2022.05.19 |
|---|---|
| [SAML Test] 4. Service Provider 생성 및 테스트 (0) | 2020.09.07 |
| [SAML Test] 3. Setup our Identity Provider (Docker환경에 설치) (0) | 2020.09.07 |
| [SAML Test] 1. Setup a Single Sign On SAML Test Environment with Docker and NodeJS (0) | 2020.09.07 |
| [SAML Test] 2. CentOS 8 nvm을 이용한 node.js 설치 (0) | 2020.09.07 |
[SAML Test] 4. Service Provider 생성 및 테스트
1. Service Provider 생성
https://medium.com/disney-streaming/setup-a-single-sign-on-saml-test-environment-with-docker-and-nodejs-c53fc1a984c9
2. Service Provider 로그인
- http://localhost:4300/login
- IdP 로그인 화면으로 이동됨

- 성공

- metadata

'IT > 기타' 카테고리의 다른 글
| 인증서 만료일자 조회 (0) | 2022.05.19 |
|---|---|
| [OAUTH2] 페이스북(facebook) OAuthCallbackListener 샘플 (0) | 2020.10.14 |
| [SAML Test] 3. Setup our Identity Provider (Docker환경에 설치) (0) | 2020.09.07 |
| [SAML Test] 1. Setup a Single Sign On SAML Test Environment with Docker and NodeJS (0) | 2020.09.07 |
| [SAML Test] 2. CentOS 8 nvm을 이용한 node.js 설치 (0) | 2020.09.07 |
[SAML Test] 3. Setup our Identity Provider (Docker환경에 설치)
1. docker 이미지 다운로드
- docker pull kristophjunge/test-saml-idp (hub.docker.com/r/kristophjunge/test-saml-idp/)
[root@localhost ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
3f1c9f57495f kristophjunge/test-saml-idp "docker-php-entrypoi 45 minutes ago Up 45 minutes 80/tcp, 0.0.0.0:48080->8080/tcp, 0.0.0.0:48443->8443/tcp testsamlidp_idp2. docker 실행
[root@localhost ~]#docker run --name=testsamlidp_idp \
-p 48080:8080 \
-p 48443:8443 \
-e SIMPLESAMLPHP_SP_ENTITY_ID=http://app.example.com \
-e SIMPLESAMLPHP_SP_ASSERTION_CONSUMER_SERVICE=http://192.168.31.100:4300/login/callback \
-e SIMPLESAMLPHP_SP_SINGLE_LOGOUT_SERVICE=http://localhost/simplesaml/module.php/saml/sp/saml2-logout.php/test-sp \
-d kristophjunge/test-saml-idp[root@localhost ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
3f1c9f57495f kristophjunge/test-saml-idp "docker-php-entrypoi 45 minutes ago Up 45 minutes 80/tcp, 0.0.0.0:48080->8080/tcp, 0.0.0.0:48443->8443/tcp testsamlidp_idp1. IdP 접속
- http://localhost:포트/simplesaml

- Authentication 탭 클릭
- Test configured authentication sources 클릭
- example-userpass 클릭
- 아래 디폴트 계정으로 로그인
| 1 | user1 | user1pass | group1 | user1@example.com |
| 2 | user2 | user2pass | group2 | user2@example.com |
| 3 | admin | secret |

'IT > 기타' 카테고리의 다른 글
| [OAUTH2] 페이스북(facebook) OAuthCallbackListener 샘플 (0) | 2020.10.14 |
|---|---|
| [SAML Test] 4. Service Provider 생성 및 테스트 (0) | 2020.09.07 |
| [SAML Test] 1. Setup a Single Sign On SAML Test Environment with Docker and NodeJS (0) | 2020.09.07 |
| [SAML Test] 2. CentOS 8 nvm을 이용한 node.js 설치 (0) | 2020.09.07 |
| Jira API token 생성 (Issue does not exist or you do not have permission to see it) (0) | 2020.06.23 |
[SAML Test] 1. Setup a Single Sign On SAML Test Environment with Docker and NodeJS
Setup a Single Sign On SAML Test Environment with Docker and NodeJS
I’m Jeffry Houser, a developer from the Polaris team in the content engineering group at Disney Streaming Services. My team builds…
medium.com
Defining Terms
The first time I was exposed to it; SAML was difficult for me to get my head around. As such, I’m going to start out with some definitions that will help you understand the pieces of a SAML application.
- Single Sign On (SSO): Any system that allows authentication code and login data to be shared across multiple applications.
- Security Assertion Markup Language (SAML): A framework, and XML schema, for implementing Single Sign On.
- Principal: The user who is attempting to gain access to our application.
- Assertions: Data about the principal which are included as part of the SAML response. Samples of this might be the user’s name, or other permission data.
- Service Provider (SP): This is the application, or system, that the user is attempting to access. We will build a simple SP as part of this article.
- Identity Provider (IdP): This is a remote application, or system, that authenticates the user and returns data back to the service provider. We’re not going to build an IdP from scratch, but I’ll show you how to set up and use a pre-built one.
- Globally Unique Identifier: A value that the IdP will use to identify an SP.
Knowing the definitions is a great start but knowing how these pieces work together is even more important and I’ll go over that next.
Review the Application Flow
This is a common flow for a SAML application:
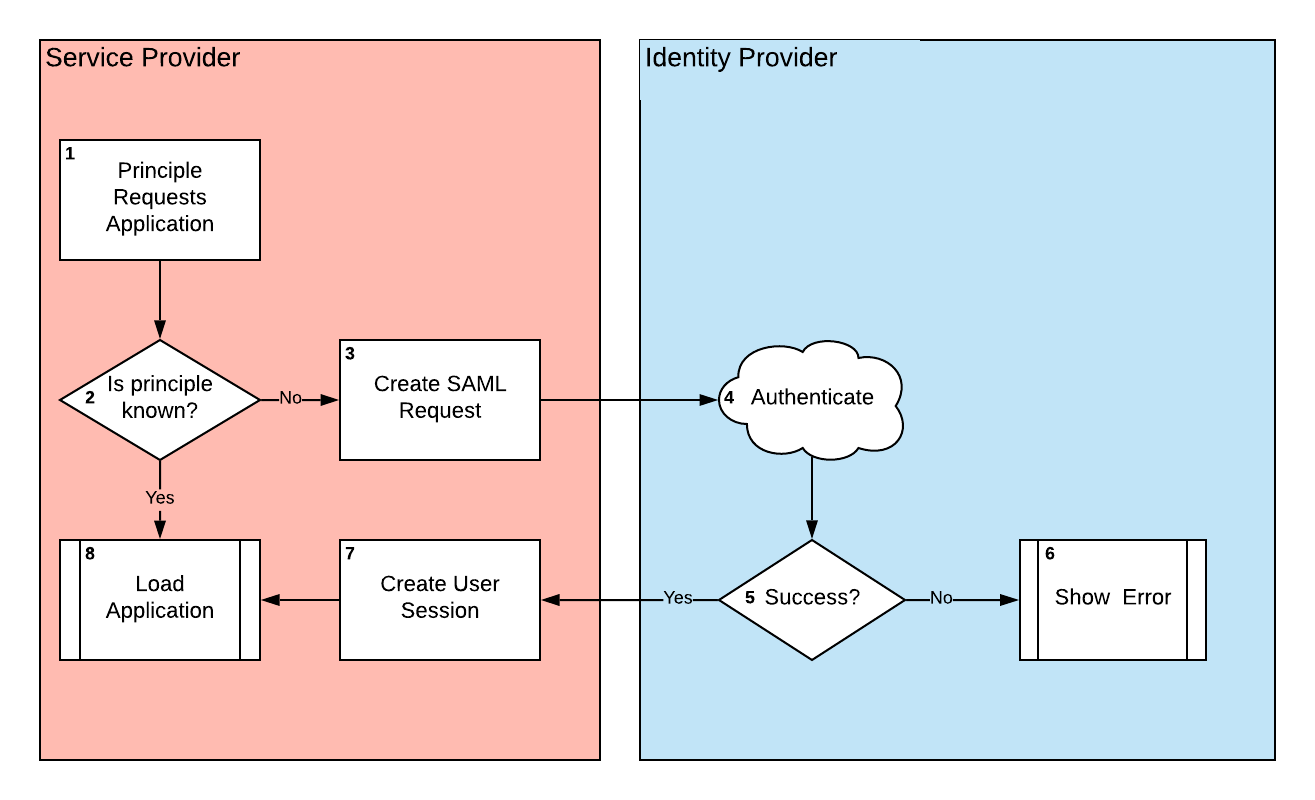
Let’s follow the flow:
- The Principal — AKA User — tries to access your Service Provider — AKA your application.
- The Service Provider checks to see if it knows the Principal. In a browser-based app, this session information would probably be stored as a cookie, but a desktop or application server may store that information in memory. If the user is known, we can load the app normally, so move onto step 8. If the user is not known, jump to step three to start the authentication process.
- If no user is known, the SP creates a SAML Request and sends that request to the IdP. This request will contain the Globally Unique Identifier so that the IdP knows which application the principal requested access to.
- Now the IdP handles the request. It will authenticate the user. It may do this based on an existing session from a previous sign in, or it may have the user login anew.
- Did the IdP successfully collect user details on the Principal? If so, go to step 7, the success set. Otherwise go to step 6 the failure step.
- If the Principal was not able to login, the IdP will handle authentication errors and the SP will know nothing about the failure.
- If the IdP successfully logged the user in, it will create a SAML response packet, including assertions about the user, and send the info back to the SP’s callback URL. The SP will use that data to create a user session.
- If the Principal authenticated properly, then load up the app and let them in.
The rest of this article will focus on steps 3 through 7.
Install Prerequisites
You’ll want to install a prerequisites before we start jumping into the code:
- Docker: Docker is a container platform that lets us easily create virtual machines with predefined code. We’re going to use it to easily create our own Identity Provider.
- NodeJS: We are going to write our Service Provider from scratch using a NodeJS and some common plugins.
- OpenSSL: OpenSSL can be used to create public and private key certificates for. Certs like these are often used for SSL on web sites, but we’re going to use them to encrypt and decrypt the packets we’re sharing between our SP and IdP.
'IT > 기타' 카테고리의 다른 글
| [SAML Test] 4. Service Provider 생성 및 테스트 (0) | 2020.09.07 |
|---|---|
| [SAML Test] 3. Setup our Identity Provider (Docker환경에 설치) (0) | 2020.09.07 |
| [SAML Test] 2. CentOS 8 nvm을 이용한 node.js 설치 (0) | 2020.09.07 |
| Jira API token 생성 (Issue does not exist or you do not have permission to see it) (0) | 2020.06.23 |
| Jira 설치 (docker) (0) | 2020.06.23 |
[SAML Test] 2. CentOS 8 nvm을 이용한 node.js 설치
1. nvm설치
- wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.35.2/install.sh
[root@localhost ~]# wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.35.2/install.sh | bash
=> Downloading nvm from git to '/root/.nvm'
=> '/root/.nvm'에 복제합니다...
remote: Enumerating objects: 288, done.
remote: Counting objects: 100% (288/288), done.
remote: Compressing objects: 100% (254/254), done.
remote: Total 288 (delta 34), reused 102 (delta 22), pack-reused 0
오브젝트를 받는 중: 100% (288/288), 146.48 KiB | 287.00 KiB/s, 완료.
델타를 알아내는 중: 100% (34/34), 완료.
=> Compressing and cleaning up git repository
=> Appending nvm source string to /root/.bashrc
=> Appending bash_completion source string to /root/.bashrc
=> Close and reopen your terminal to start using nvm or run the following to use it now:
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
[ -s "$NVM_DIR/bash_completion" ] && \. "$NVM_DIR/bash_completion" # This loads nvm bash_completion
[root@localhost ~]# source .bashrc
[root@localhost ~]# nvm --version
0.35.2
2. node.js 설치
- 최신 LTS 버전으로 설치 : nvm install --lts
[root@localhost ~]# nvm install --lts
Installing latest LTS version.
Downloading and installing node v12.18.3...
Downloading https://nodejs.org/dist/v12.18.3/node-v12.18.3-linux-x64.tar.xz...
##################################################################################################################################################################################################################################### 100.0%
Computing checksum with sha256sum
Checksums matched!
Now using node v12.18.3 (npm v6.14.6)
Creating default alias: default -> lts/* (-> v12.18.3 *)
[root@localhost ~]# nvm list
-> v12.18.3 *
default -> lts/* (-> v12.18.3 *)
iojs -> N/A (default)
node -> stable (-> v12.18.3 *) (default)
stable -> 12.18 (-> v12.18.3 *) (default)
unstable -> N/A (default)
lts/* -> lts/erbium (-> v12.18.3 *)
lts/argon -> v4.9.1 (-> N/A)
lts/boron -> v6.17.1 (-> N/A)
lts/carbon -> v8.17.0 (-> N/A)
lts/dubnium -> v10.22.0 (-> N/A)
lts/erbium -> v12.18.3 *
- 설치 확인
[root@localhost ~]# node -v
v12.18.3
[root@localhost ~]# npm -v
6.14.6
'IT > 기타' 카테고리의 다른 글
| [SAML Test] 3. Setup our Identity Provider (Docker환경에 설치) (0) | 2020.09.07 |
|---|---|
| [SAML Test] 1. Setup a Single Sign On SAML Test Environment with Docker and NodeJS (0) | 2020.09.07 |
| Jira API token 생성 (Issue does not exist or you do not have permission to see it) (0) | 2020.06.23 |
| Jira 설치 (docker) (0) | 2020.06.23 |
| [AWS] EC2 SecureCRT 로 접속하기 (0) | 2020.06.22 |
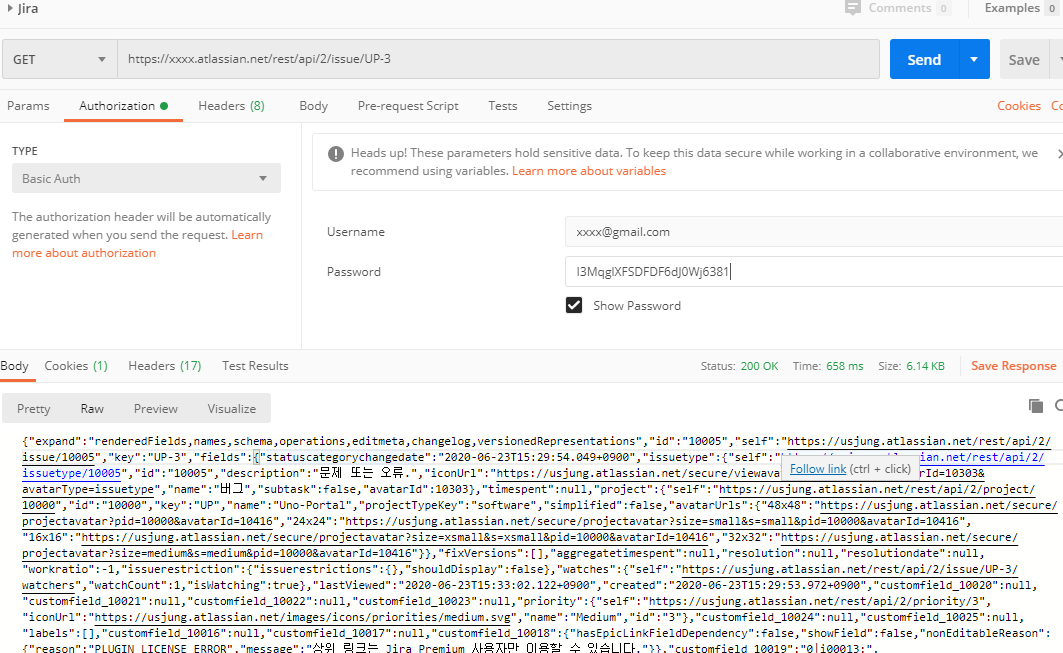
Jira API token 생성 (Issue does not exist or you do not have permission to see it)
*여기에 설명이 잘 나와 있습니다 -> https://confluence.atlassian.com/cloud/api-tokens-938839638.html
현상 : Issue does not exist or you do not have permission to see it 오류 발생함.
1. API 토큰 화면 접속 : https://id.atlassian.com/manage-profile/security/api-tokens
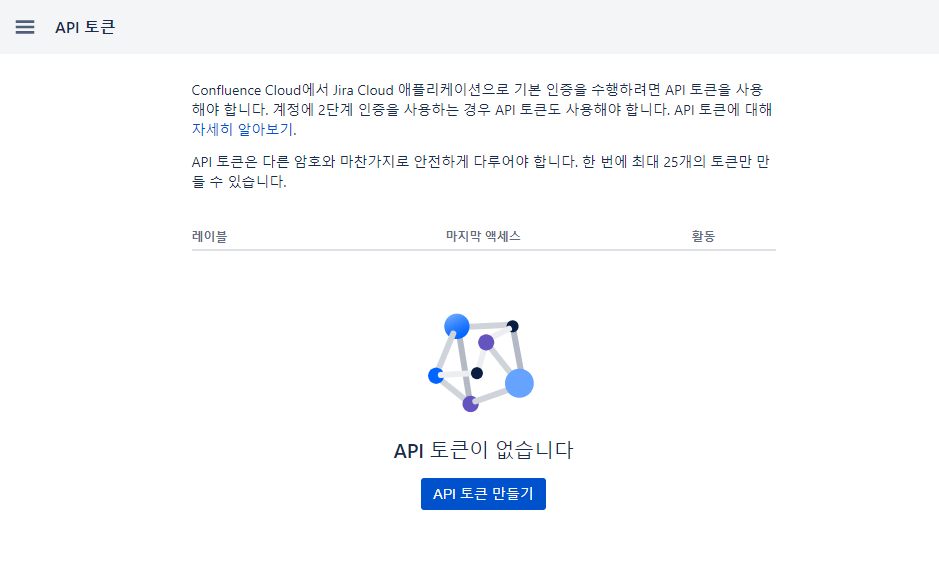
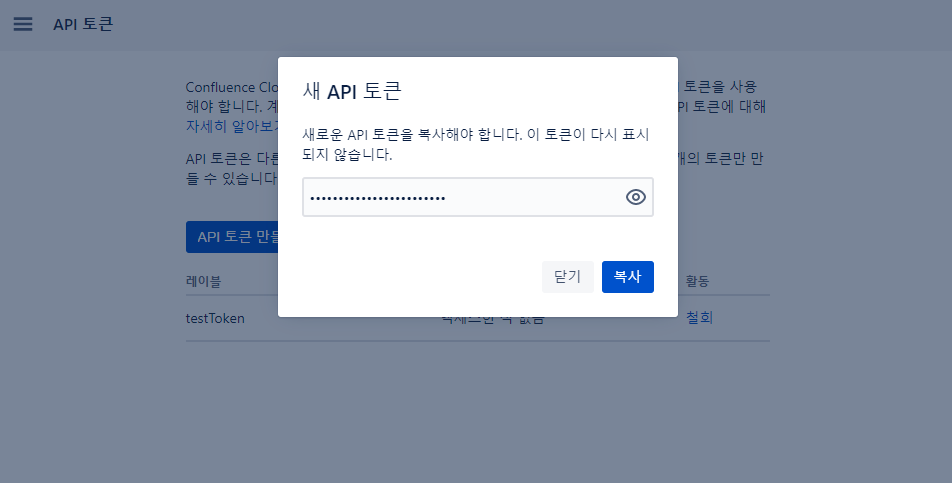
2. 토큰 생성
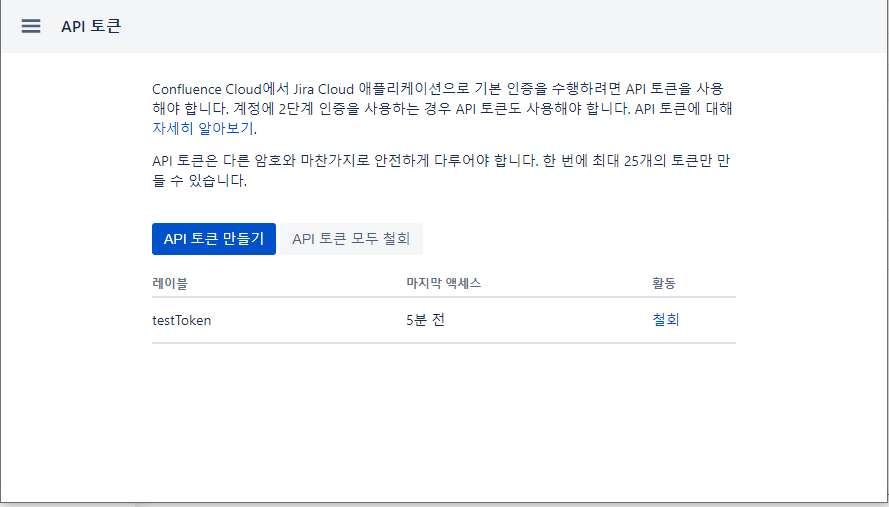
3. 토큰 조회
4. Postman 으로 테스트 (Get issue : GET /rest/api/2/issue/{issueIdOrKey})
- JIRA Server platform REST API reference : https://docs.atlassian.com/software/jira/docs/api/REST/8.4.2/?_ga=2.93052573.1639889686.1571238783-647032862.1567516016
'IT > 기타' 카테고리의 다른 글
| [SAML Test] 1. Setup a Single Sign On SAML Test Environment with Docker and NodeJS (0) | 2020.09.07 |
|---|---|
| [SAML Test] 2. CentOS 8 nvm을 이용한 node.js 설치 (0) | 2020.09.07 |
| Jira 설치 (docker) (0) | 2020.06.23 |
| [AWS] EC2 SecureCRT 로 접속하기 (0) | 2020.06.22 |
| json-server (docker) (0) | 2020.06.17 |
Jira 설치 (docker)
- OS : CentOS8
- Docker
Server : Docker Engine - Community
Version: 18.09.1
API version: 1.39 (minimum version 1.12)
Go version: go1.10.6
Git commit: 4c52b90
Built: Wed Jan 9 19:06:30 2019
OS/Arch: linux/amd64
Experimental: false
1. Jira 이미지 다운로드
[root@localhost ~]# docker pull cptactionhank/atlassian-jira-software:latest
latest: Pulling from cptactionhank/atlassian-jira-software
e7c96db7181b: Pull complete
f910a506b6cb: Pull complete
c2274a1a0e27: Pull complete
d7c1375c56aa: Pull complete 126MB/380MB
7d152efddb87: Pull complete
Digest: sha256:4d21c48c3aff4649e5c3418114fcd1d18e92994d84723597289bb580951d57df
Status: Downloaded newer image for cptactionhank/atlassian-jira-software:latest2. Jira 설치
[root@localhost ~]# docker run --name jira -itd --restart=no \
> -p 38080:8080 \
> -v /data/jira:/var/atlassian/jira \
> -u root \
> --env "CATALINA_OPTS= -Xms1024m -Xmx1024m -Datlassian.plugins.enable.wait=300" \
> cptactionhank/atlassian-jira-software:latest
ca8c3e85b82437e3a45db10b229c97d511149cd5557524560d39528c1bc0654a[root@localhost ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
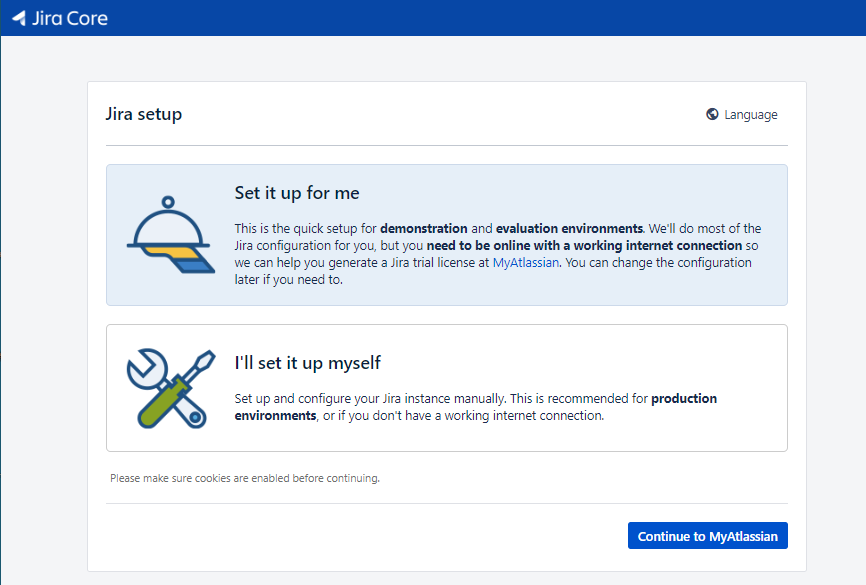
ca8c3e85b824 cptactionhank/atlassian-jira-software:latest "/docker-entrypoint. 2 minutes ago Up 2 minutes 0.0.0.0:38080->8080/tcp jira3. Jira 설치 확인. Continue to MyAtlassian 클릭.
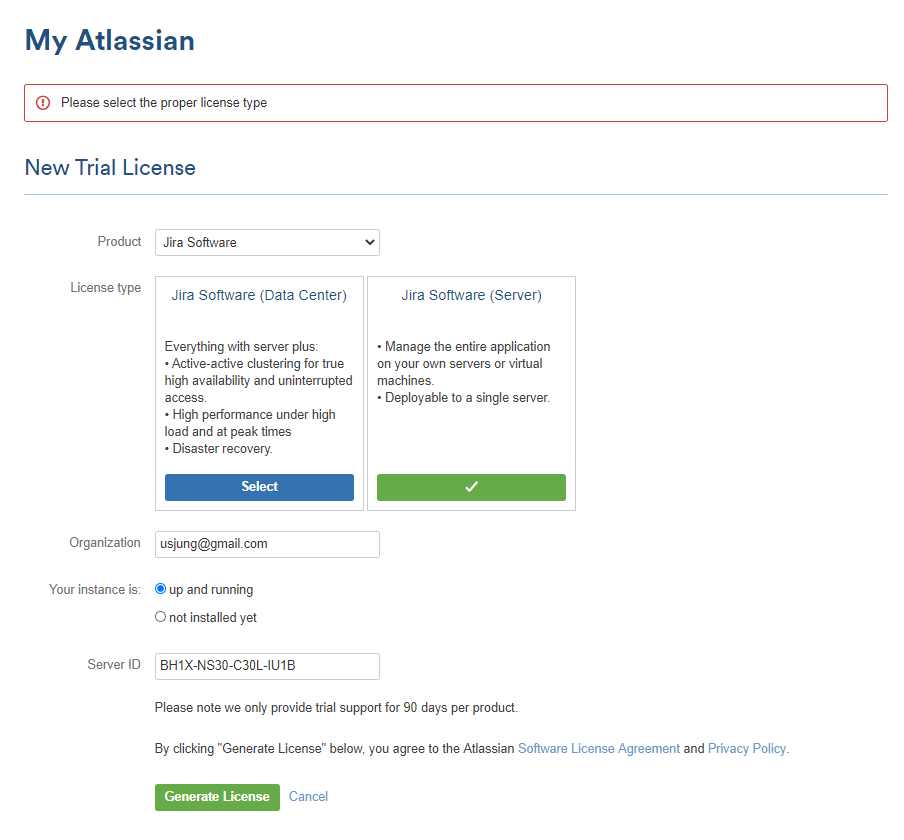
4. 트라이얼 라이센스 생성. Jira Software (Server) 선택. Generate License 클릭
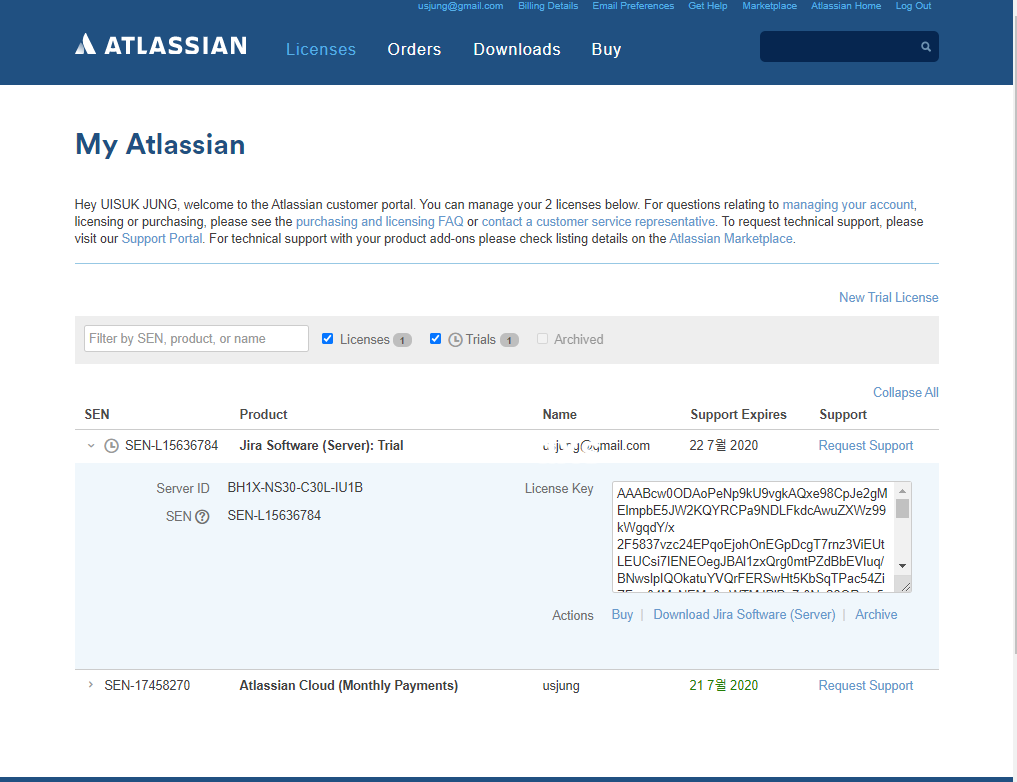
5. 완료
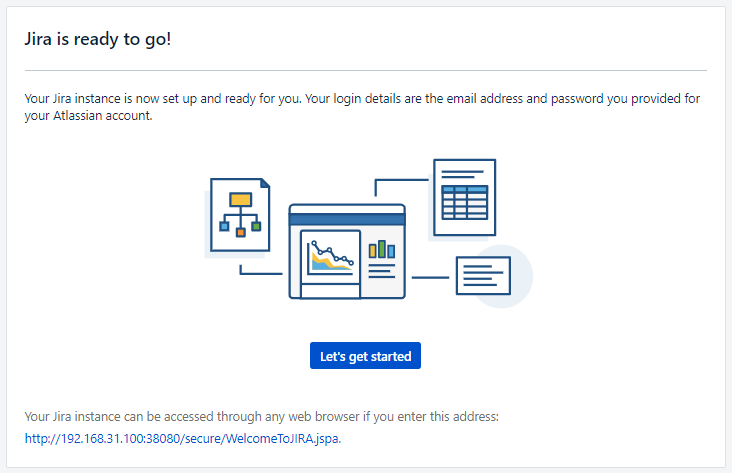
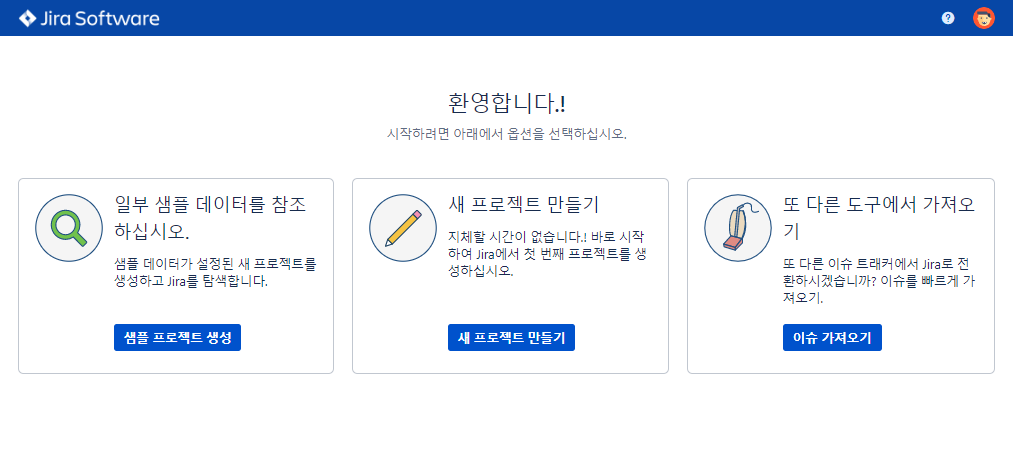
'IT > 기타' 카테고리의 다른 글
| [SAML Test] 1. Setup a Single Sign On SAML Test Environment with Docker and NodeJS (0) | 2020.09.07 |
|---|---|
| [SAML Test] 2. CentOS 8 nvm을 이용한 node.js 설치 (0) | 2020.09.07 |
| Jira API token 생성 (Issue does not exist or you do not have permission to see it) (0) | 2020.06.23 |
| [AWS] EC2 SecureCRT 로 접속하기 (0) | 2020.06.22 |
| json-server (docker) (0) | 2020.06.17 |
